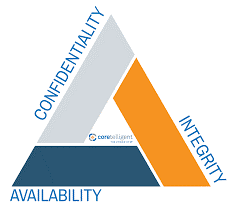
CIA
Confidentiality, Integrity, and Availability, often referred to as the CIA triad, are three core principles of information security:
Confidentiality:
· Definition: Ensuring that information is only accessible to authorized individuals or entities.
· Objective: Protecting sensitive data from unauthorized access or disclosure.
Integrity:
· Definition: Ensuring the accuracy, reliability, and trustworthiness of data throughout its lifecycle.
· Objective: Preventing unauthorized or accidental modification, deletion, or alteration of data.
Availability:
· Definition: Ensuring that information and systems are accessible and usable when needed by authorized users.
· Objective: Preventing disruptions or downtime, ensuring timely access to data and resources.
In summary, the CIA triad represents the fundamental principles of securing information and systems by maintaining confidentiality, integrity, and availability. These principles serve as a foundation for designing and implementing effective security measures in various contexts, such as IT systems, networks, and data management.
Comments
Post a Comment